Centralized cryptocurrency exchanges have always been a target for hackers, with increasingly sophisticated malicious actors finding ever more ingenious ways to loot their multimillion-dollar holdings.
Over half a billion dollars was lost to hacks and fraud in Q2 of 2024, according to recent research, with the bulk of that accounted for by centralized crypto financial institutions like exchanges.
“Some exchanges don’t adequately use cold wallets to protect user funds,” Gate.io Chief Security Officer D told Decrypt. “They fail to update and patch software vulnerabilities in a timely manner, and they don’t publicly disclose security audit results and vulnerability reports.”
One of the top 10 crypto exchanges by volume, Gate.io has developed a “multi-layered security approach” in order to safeguard the accounts of its 16 million users, along with proactive strategies to address the threat posed by hackers.
Proactively addressing threat vectors
There are four main attack vectors for centralized exchanges: hacks, phishing attacks, internal threats, and software vulnerabilities. Phishing attacks are when a user is tricked by a bad actor into giving away their account information, either directly or via phishing links. Internal threats relate to individuals within organizations going rogue and becoming bad actors, or their negligence creating opportunities for hackers to take user funds. When an attack is based on a software vulnerability, it means that a bad actor has exploited the platform’s own code.
To combat these threats, Gate.io told Decrypt, the exchange employs a team of dedicated security experts who use a risk-based strategy to “uphold the highest levels of user asset protection.” Whereas some exchanges take a reactive approach to security, only focusing on security when it becomes a problem, Gate.io proactively audits and stress tests their platform against potential threats regularly, on an ongoing basis.
Gate.io “actively collaborates with regulatory authorities to ensure the platform meets local and international regulations,” the exchange’s Chief Security Officer said, explaining that the exchange employs security measures including multi-factor authentication (MFA), cold wallet storage and advanced encryption technology. It also engages in regular security audits and security awareness training to prevent internal threats, they added.
Gate.io’s ‘unique security layers’
“We add unique security layers on top of traditional security measures, as well as providing convenient security tools for users,” the Chief Security Officer told Decrypt.
Those tools include Bind IP, a feature that enables users to bind their account to specific IP addresses, or a range of IP addresses. “This significantly enhances account security, especially in preventing remote attacks,” the Chief Security Officer said. Even in “unsafe environments, such as during a hijacking,” if a hacker obtains a user’s login credentials, they can’t access the account from an unauthorized IP address, they added.
In addition, they said, “We have implemented a phishing code design, allowing users to recognize phishing attempts more easily through custom sologo welcome forms.”
And even if a hacker were able to access a user’s account, Gate.io users have the ability to “set additional special passwords to unlock withdrawals and transactions,” the exchange’s Chief Security Officer explained, adding that the feature ensures that security-conscious users can limit access to their funds.
Proof of reserves
As well as directly targeting the threat posed by hackers, Gate.io has committed to maintaining transparent proof of reserves at all times, in order to bring peace of mind to its customers. Its proof of reserves solution combines zero-knowledge proof technology with Merkle Tree, a Gate.io representative told Decrypt.
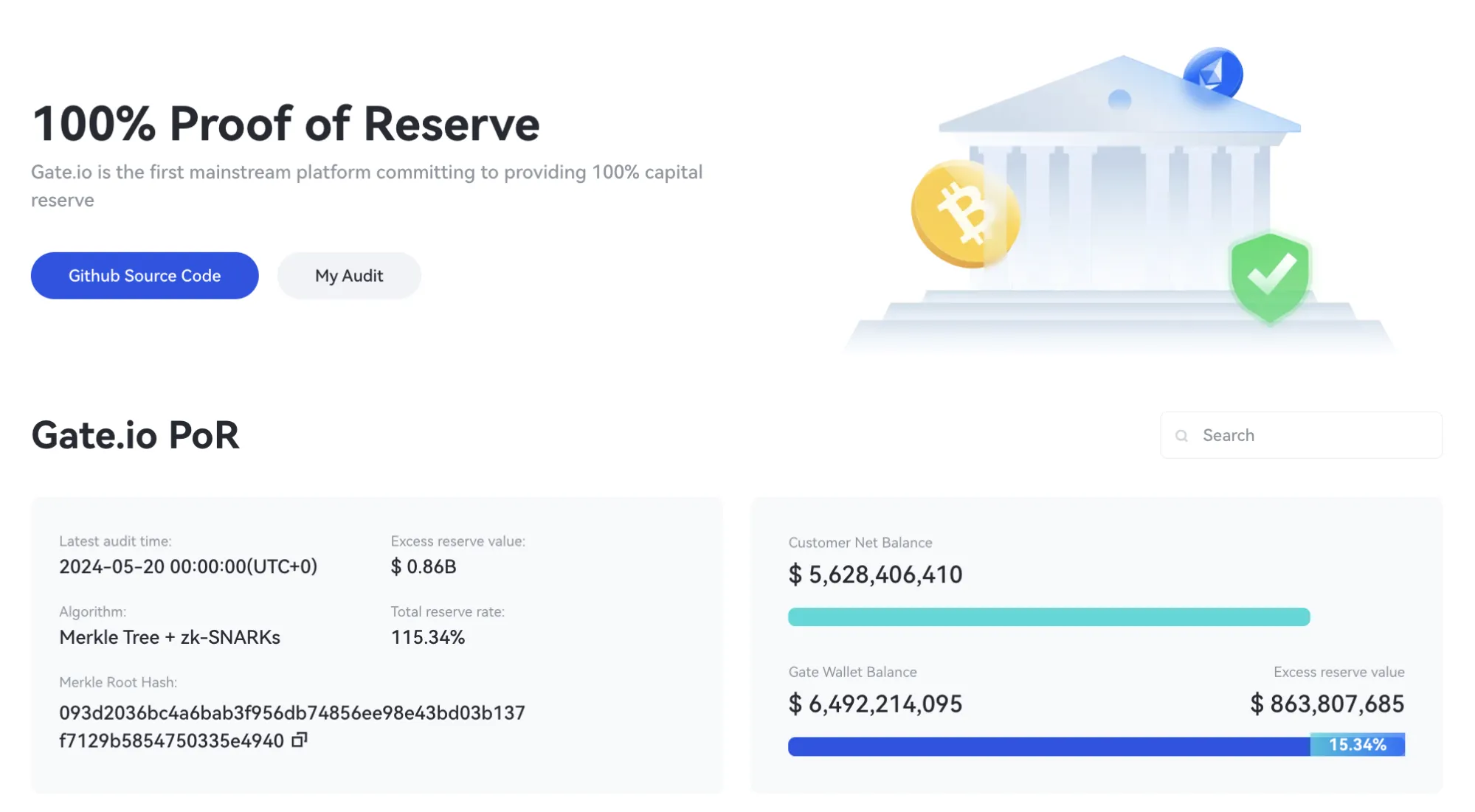
“Merkle Tree can effectively verify the integrity of large amounts of data and includes all users’ asset information without including net negative assets,” the Chief Security Officer explained, adding that, “Zero-knowledge proof is used to prove that specific data belongs to this Merkle Tree without disclosing any other information.”
In hopes of boosting trust and transparency in the industry, the Chief Security Officer added, Gate.io has also open-sourced their proof of reserve solution.